
ThreatQuotient
Founded Year
2013Stage
Acquired | AcquiredTotal Raised
$105.86MAbout ThreatQuotient
ThreatQuotient operates within the cybersecurity industry, offering a Threat Intelligence Platform (TIP) for threat detection, investigation, and response, alongside services for implementing threat intelligence and automating security operations. The company serves sectors including technology, financial services, and government agencies. It was founded in 2013 and is based in Ashburn, Virginia. In June 2025, ThreatQuotient was acquired by Securonix.
Loading...
ESPs containing ThreatQuotient
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The threat intelligence platforms market offers solutions to address the challenges faced by security teams in protecting their organizations from cyber threats. These platforms aggregate and correlate data from various sources, including internal security logs, external threat feeds, dark web monitoring, and open-source intelligence. The data is enriched with AI to create profiles & patterns of m…
ThreatQuotient named as Challenger among 15 other companies, including CrowdStrike, Tata Consultancy Services, and Palo Alto Networks.
Loading...
Research containing ThreatQuotient
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned ThreatQuotient in 1 CB Insights research brief, most recently on Jan 25, 2023.
Expert Collections containing ThreatQuotient
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
ThreatQuotient is included in 2 Expert Collections, including Regtech.
Regtech
1,611 items
Technology that addresses regulatory challenges and facilitates the delivery of compliance requirements. Regulatory technology helps companies and regulators address challenges ranging from compliance (e.g. AML/KYC) automation and improved risk management.
Cybersecurity
11,352 items
These companies protect organizations from digital threats.
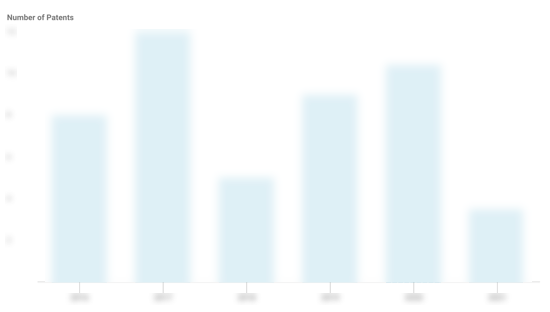
ThreatQuotient Patents
ThreatQuotient has filed 3 patents.
The 3 most popular patent topics include:
- adware
- classes of computers
- computer network security
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
1/25/2021 | 6/25/2024 | Parallel computing, Data management, Computer security, Open formats, Classes of computers | Grant |
Application Date | 1/25/2021 |
|---|---|
Grant Date | 6/25/2024 |
Title | |
Related Topics | Parallel computing, Data management, Computer security, Open formats, Classes of computers |
Status | Grant |
Latest ThreatQuotient News
Jul 4, 2025
Collaboration is Key: How to Make Threat Intelligence Work for Your Organisation This piece is by Chris Jacob, VP, Global Field Operations at ThreatQuotient, a Securonix Company Recent cyberattacks on retailers in the UK and US have shifted to target the financial and now the aviation sector, with news on breaches reaching headlines almost daily. These stories track how today’s threat actors operate: they are strategic, pivot quickly, exploit weak links, and are highly opportunistic. This opportunism means that if threat actors discover an unlocked door in one business within an industry, they will try every door within that industry to find a common weakness. As shrewd businessmen, they are more likely to target industries rich in customer data and personally identifiable information (PII) and with large, complex supply chains – such as retail and finance. Industry-specific weaknesses and single points of failure within a supply chain are cybersecurity soft spots that regulations such as The Digital Operational Resilience Act (DORA) within the financial sector and the NIS2 Directive aim to address directly: both emphasising structured information flows, sector-level cooperation, and operational resilience. One valuable tool for meeting these requirements and increasing pro-activity is through the tactic of threat intelligence sharing. Shifting From Isolation to Collaboration Cybersecurity teams are justifiably cautious to share threat intelligence too broadly as it can lead to indicators being released prematurely or posted into the wrong forum, and could alert threat actors to change their tactics. However, working in isolation against threat actor networks, such as Scattered Spider, leaves cybersecurity teams at a distinct disadvantage. Cyberattacks, increasing in scale and sophistication, are being launched persistently. According to recent research by Everfox, FS&B organisations are facing 114 cyberattacks a week – a staggering number of attacks, and a rich pool of actionable threat intelligence to warn and prepare other organisations, if securely shared. The Power of Trusted Communities The good news is that facilitators for secure, structured intelligence sharing already exist. Sector-specific communities like FS-ISAC (for financial services) and RH-ISAC for (retail and hospitality) provide trusted environments where verified members can share threat data safely. These communities use standardised formats like STIX/TAXII to automate and anonymise data exchange. This allows organisations to contribute and consume intelligence without exposing sensitive internal details. These communities comprise both large and small organisations. Typically, larger organisations have more mature security operations and can share vast amounts of threat intelligence, which is an invaluable resource for smaller organisations. Smaller organisations, usually distributed at different points within the supply chain, are also able to verify the threat intelligence from the front lines – and alert to novel attacks. This enables organisations to gain visibility over multiple supply chains and apply proactive and predictive reasoning to their own environments. Threat Intelligence Sharing communities can also be created within advanced threat intelligence sharing platforms, enabling security teams to select organisations and filter through threat intelligence to curate their feed. Strengthening Community Another benefit of joining an FSISAC – or building your own threat intelligence community – is that in-person meetups are encouraged. CISOs and security teams can hold lonely positions within a company, with a considerable weight on their shoulders, and becoming part of a threat intelligence sharing community can be a good way to alleviate this sense of isolation and feel united with fellow professionals under a common cause. Meeting peers face-to-face also establishes trust and enables cybersecurity professionals to verify the people they are sharing threat intelligence information with. In the age of AI-enabled deepfakes, professionals can never be too careful. From Drinking from the Firehose to Putting out Fires A challenge with joining threat intelligence sharing communities is that a lot of threat information is generated and needs to be shared daily. For already resource-stretched teams, it can be extra work to pull together, share a threat intelligence report, and filter through the incredible volumes of information. Particularly for smaller organisations, it can be a bit like drinking from a firehose. In this context, an advanced threat intelligence platform (TIP) can be invaluable. A TIP has the capabilities to collect, filter, and prioritise data, helping security teams to cut through the noise and act on threat intelligence faster. TIPs can also enrich the data with additional context, such as threat actor TTPs (Tactics, Techniques, and Procedures), indicators of compromise (IOCs), and potential impact, making it easier to understand and respond to threats. Furthermore, an advanced TIP can have the capability to automatically generate threat intelligence reports, ready to be securely shared into the organisation’s threat intelligence sharing community. Secure threat intelligence sharing reduces risk, accelerates response, and builds resilience across entire ecosystems. If you’re not already part of a trusted intelligence-sharing community, it is time to join. And if you are, do contribute your own valuable threat information. In cybersecurity, we’re only as strong as our weakest link, and our most silent partner. Share this:
ThreatQuotient Frequently Asked Questions (FAQ)
When was ThreatQuotient founded?
ThreatQuotient was founded in 2013.
Where is ThreatQuotient's headquarters?
ThreatQuotient's headquarters is located at 20130 Lakeview Center Plaza, Ashburn.
What is ThreatQuotient's latest funding round?
ThreatQuotient's latest funding round is Acquired.
How much did ThreatQuotient raise?
ThreatQuotient raised a total of $105.86M.
Who are the investors of ThreatQuotient?
Investors of ThreatQuotient include Securonix, Virginia Venture Partners, New Enterprise Associates, Blu Venture Investors, Cisco Investments and 15 more.
Loading...
Loading...

